Making limited use of Citrix SmartAccess without universal licenses can still benefit your Citrix environment. If you are using Citrix Gateway as ICA Proxy only than this article is for you. Learn how to configure SmartAccess in a Citrix Virtual Apps and Desktop environment for users connecting through Citrix Gateway (NetScaler Gateway). You do NOT need Universal licenses to use at least some of the SmartAccess features!
Enabling the full set of SmartAccess features revolves around the ICA Only setting on a vServer.
As per Citrix:
“When set to ON, it implies Basic mode where the user can log on using either Citrix Receiver or a browser and get access to the published apps configured at the XenApp/XenDesktop environment […]. Users are not allowed to connect using the NetScaler Gateway Plug-in and end point scans cannot be configured. The numbers of users that can log in and access the apps are not limited by the license in this mode.”
Most articles on the Internet state that you have to enable SmartAccess mode (change the ICA Only setting from true to false) on the vServer in order to use SmartAccess (here for example). This is both true and not true. There are two reasons why this can be confusing:
- The features that make up SmartAccess;
- The terminology used: Basic Mode, ICA Proxy and SmartAccess (mode)
Let’s take a look at the features of SmartAccess first:
- Citrix Studio: Access policy on the Delivery Group
An Access policy allows you to show or hide all applications in a Delivery Group when connecting through Citrix Gateway. You can add a filter for more granular control. If you want to work with filters, SmartAccess mode needs to be enabled on the Citrix Gateway vServer. If your organization does not require any Endpoint Analysis scans than SmartAccess mode is not required, but your configuration is limited to either “show” or “hide” applications when a user connects through Citrix Gateway, nothing more.
- Citrix Studio/Active Directory: Access Control filters on Citrix policies
 An Access Control filter determines whether or not a user policy is applied to connections made through Citrix Gateway. You can add a filter for more granular control. If you want to work with filters, SmartAccess mode needs to be enabled on the Citrix Gateway vServer. If your organization does not require any Endpoint Analysis scans than SmartAccess mode is not required, but your configuration is limited to either “apply” or “deny” policies when a user connects through Citrix Gateway, nothing more.
An Access Control filter determines whether or not a user policy is applied to connections made through Citrix Gateway. You can add a filter for more granular control. If you want to work with filters, SmartAccess mode needs to be enabled on the Citrix Gateway vServer. If your organization does not require any Endpoint Analysis scans than SmartAccess mode is not required, but your configuration is limited to either “apply” or “deny” policies when a user connects through Citrix Gateway, nothing more. - Citrix Gateway: Endpoint Analysis (EPA) scans
If your organization requires pre-authentication scans using a Preauthentication policy or post-authentication scans (within a Session policy) then SmartAccess mode is required. For example, when trying to bind a Preauthentication policy to your vServer without SmartAccess mode enabled the following error is displayed.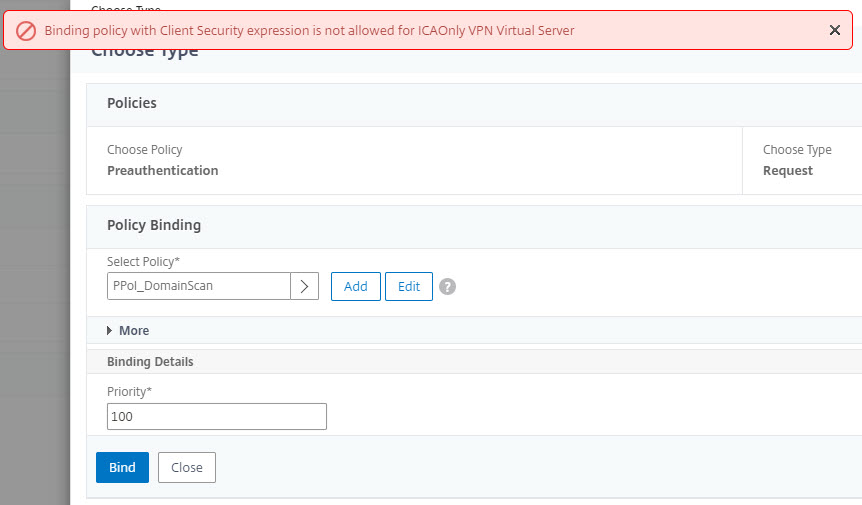
Now let’s take a look at some of the terminology used. Citrix describes SmartAccess as follows:
“SmartAccess allows you to control access to published applications and desktops on a server through the use of Citrix Gateway session policies. You use pre-authentication and post-authentication checks as a condition, along with other conditions, for access to published resources. Other conditions include anything you can control with a Citrix Virtual Apps and Desktops policy, such as printer bandwidth limits, user device drive mapping, clipboard, audio, and printer mapping. You can apply a Citrix Virtual Apps and Desktops policy based on whether or not users pass an Citrix Gateway check.”
So the SmartAccess feature-set is a combination between configurations on Citrix Gateway (the Endpoint Analysis scans) and Citrix Virtual Apps and Desktops (Delivery Group Access policies and Citrix policies). As mentioned, Endpoint Analysis scans and making use of filters in an Access policy and Access Control filter require SmartAccess mode to be enabled.
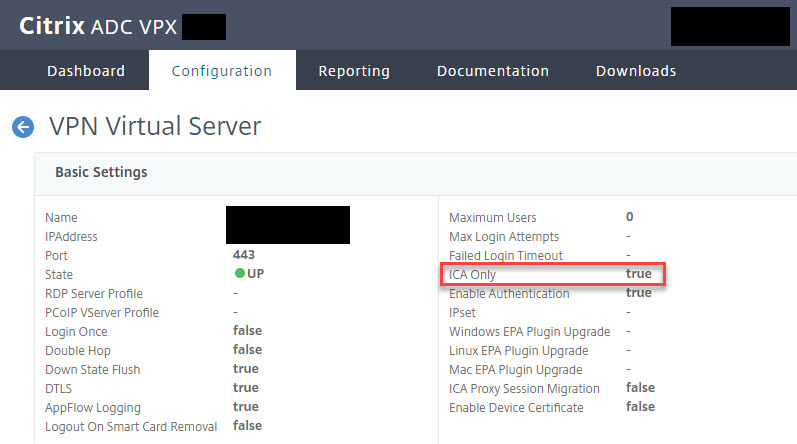
Other wording that is important to understand is that if SmartAccess mode is disabled (= ICA Only set to true on the vServer) you are running in Basic Mode (also called ICA proxy).
So what do you need to configure in your environment in order for SmartAccess to work without Universal licenses?
NetScaler Gateway
The Citrix Gateway vServer itself actually does not need any configuration, assuming that an ICA session can be launched successfully via NetScaler. ICA Only can be set to true. Just be aware that you will not be able to use Endpoint Analysis scans (pre- and post-authentication).
StoreFront
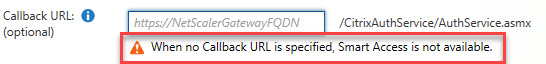
Make sure that you enter a callback URL to your Citrix Gateway configuration.
In all fairness, when no callback URL has been configured, a very clear warning message is displayed.
Delivery Controller
Make sure that the XML Service trusts requests that are sent without explicit authentication. Enable TrustRequestsSentToTheXmlServicePort on the Delivery Controller.
To check whether or not this setting has already been enabled, open a PowerShell window on a Delivery Controller and enter the following two commands:
asnp citrix*
followed by
Get-BrokerSite
The setting TrustRequestsSentToTheXmlServicePort should be set to true.
In case it is not, execute the following two commands to enable it:
asnp citrix*
followed by
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $true
Studio / Active Directory
Now that the prerequisites have been dealt with you can start using the SmartAccess features.
In Studio, configure an Access policy (without filters) if your organization requires it.
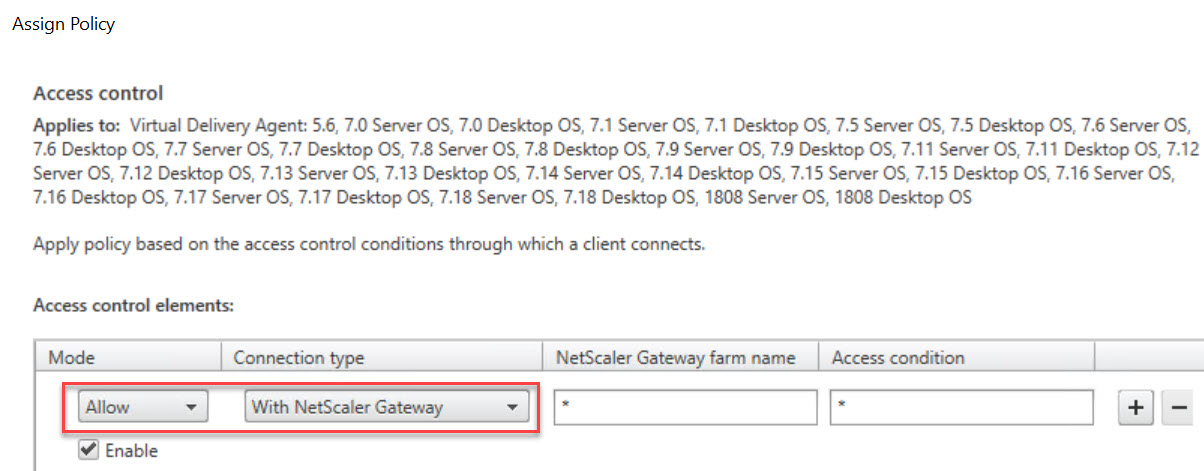
In Studio or Active Directory, add an Access Control filter to a Citrix policy (without specifying filters except for the * as a wildcard for both the farm name and the access condition).
Do not let the Allow or Deny mode confuse you. Allow simply means that the settings in the policy are to be applied. In case the policy settings prohibit something, setting the mode to allow means that you allow the policy to prohibit something when connecting via Citrix Gateway. If you choose Deny, the settings prohibiting something will not be applied to users connecting via Citrix Gateway.
Remember that Access Control filters apply to user settings only!
Let’s take a look at some examples how to use SmartAccess.
Example 1: enable drive mapping internally for all users, but not through Citrix Gateway
This configuration can be handled by one single policy.
Create a new policy and configure the settings in the File Redirection section as required in your organization.
Add an Access Control filter and set all Citrix Gateway connections to Deny.
The result is that no local drives will be available within the user’s session when connecting through Citrix Gateway. Local drives are available when connecting internally through StoreFront.
Example 2: enable drive mapping internally for all users, but not through Citrix Gateway, except for some users
This configuration requires two policies.
First we create a policy where we allow drive mapping for all users (I know that drive mapping is allowed by default. This is just an example).
No filter is applied.
Now we create a second policy where we prohibit all drive mapping.
We will use two filters. We set one filter for connections through Citrix Gateway. Set the mode to Allow so the settings in the profile apply when connecting through Citrix Gateway.
Now add a second filter for User or Group. Add an Active Directory user group for which drive mapping through Citrix Gateway is allowed. Set the mode to Deny (because we do not want the settings within this policy to be applied to these users).
This policy now has two filters:
Last but not least, make sure that you set the priority correctly. The policy prohibiting the drive mapping should be higher than the one allowing it.
For more information on SmartAccess (and SmartControl, which I did not mention in this article on purpose) please see the following excellent articles by two esteemed Citrix CTPs:
- Carl Stalhood: SmartAccess / SmartControl – NetScaler Gateway 12
- George Spiers: SmartControl and SmartAccess
I hope this article was of some help to you.
Dennis Span works as a Principal Account Technology Strategist at Cloud Software Group in Vienna, Austria. He holds multiple Citrix certifications (CCE-V). Dennis has been a Citrix Technology Advocate (CTA) since 2017 (+ one year as Citrix Technology Professional, CTP). Besides his interest in virtualization technologies and blogging, he loves spending time with his family as well as snowboarding, playing basketball, and rowing. He is fluent in Dutch, English, German, and Slovak and speaks some Spanish.












Hello Denis,
which XenDesktop license do you need to implement this? Virtual Apps Premium
Hi Dim,
No special license/version is required. Citrix NetScaler/Citrix ADC can be used in ICA Proxy mode in any of the CVAD versions (https://www.citrix.com/products/citrix-virtual-apps-and-desktops/feature-matrix.html).
Hi Dennis,
Nice article, however it does not work if no callback URL is supplied. Let me explain why I needed it with no callback URL – if no callback is specified – user can connect from multiple AG and still hit same storefront and same store.
Also on Example 1, the third image shows Deny and it should be Allow 😉
Hi Plamen,
Correct, a callback URL has to be configured in order for Smart Access to work. I did mention that though. Secondly, in Example 1 I aim to deny drive mapping through NetScaler Gateway. In my example drive mapping is allowed except for connections through NetScaler Gateway (deny). The image is therefore correct.
Nice article, some are saying that you can use a dummy NSG vip only if the storefront servers cant reach the DmZ nsg vip. My question, if you know is if connections are coming in on the real NSG vip the you have smart access enabled with the call back URL which some are saying point it to a layer 2 dummy vip that is on the Subnets as storefront subnet. How does it understand how to call back and check if the authentication was coming in on the dummy NSG vip? Does it just understand that that you just came from a Netscaler gateway because it’s having to do a callback based on the configuration set in the storefront setting “remote locations” portions?
Nice article Dennis, are you aware of creating a dummy vip for a call back URL? I am reading some material out there that states you can do a dummy call back URL. However I am not sure how this works if the dummy vip isn’t the real NSG vip they are coming throug
Yea, if he denied Drive mapping meaning the Policy is denied( Not applying) the image is correct. I can see where it is confusing. Deny means deny the filter, and allow is to allow the filer. Like you said ” Do not let the Allow or Deny mode confuse you. Allow simply means that the settings in the policy are to be applied. In case the policy settings prohibit something, setting the mode to allow means that you allow the policy to prohibit something when connecting via Citrix Gateway. If you choose Deny, the settings prohibiting something will not be applied to users connecting via Citrix Gateway.”